Freenigma, email encryption done right
August 24, 2006During the last two days I had a chance to test drive Freenigma, the recently released email encryption service for webmail users. What I like more of Freenigma is its “Johnny can encrypt” approach. For the average Johnny, cryptography is insanely complex, while Freenigma makes a point of hiding this complexity under a very simple user interface.
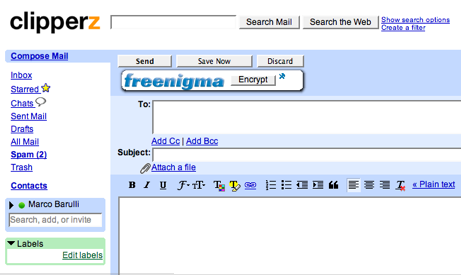
[UPDATE 2013] Link to Freenigma removed since the website is no longer available.
Using the service you are barely aware that you now own a pair of public and private keys, or that you are exchanging encrypted session keys with the recipients of your messages, and so on.
Everything looks smooth and simple from the installation of the Firefox extension to the activation of the service. If you can handle the list of your friends in a IM client or managing your contacts in a social network then you can encrypt your email messages with Freenigma.
Freenigma still has some limitations (mainly related to attachments and browser support), but I’m sure I’m going to be a regular user of this simple, powerful (and free) service.
Yesterday Stefan Richter from Freiheit - Freenigma is a joint venture of Freiheit and g10code - was so kind to answer few questions about the service and the technology behind it. Here is a transcript of the interview.
[Clipperz]: Firefox 2.0 Beta is out since few weeks and it’s already quite popular. However Freenigma is only supporting Firefox 1.5. What are your plans with regard to Firefox 2.0 and Safari?
[SR]: We will test our extension this week in Firefox 2.0. So our aim is to support the new version asap. And we think about versions for Safari and Internet Explorer.
But you can use Freenigma not only for Web-Mailers: Werner Koch, the developer and maintainer of GnuPG, wrote a C
reference implementation for a Freenigma client. This will soon be released as a command-line tool and a C library. We already have Perl bindings and with the C library available it will be easy to provide Python, Perl and whatever-you-like-language bindings.
This means you can encrypt files on your disk with the same freenigma account that you use for your Web-Mail. With a shell script! :-)
Or you can use it with your favorite mail client, like Mutt, Kmail or Evolution. (We already have a Kmail plugin for Freenigma).
You see, we really want to “Encrypt the plane/t”. ;-)
[Clipperz]: Your “Terms of Use” document contains a stunning bit of information: strong encryption is illegal in France! Is that really true or just a cautious statement?
[SR]: Yes, it is true. France does not allow strong encryption for their citizens. It is really difficult to find out which countries around the world are prohibiting cryptography.
[Clipperz]: Subjects of email messages are not encrypted by Freenigma. Wouldn’t be more secure to encrypt them as well?
[SR]: Hmm. This makes it really difficult to read the subject lines in your inbox. The subject line would get quite big because it would be a complete PGP message block. But maybe we could pack it with the mail body and extract it in the decryption process?! Hmm, then it would not be very compatible with GUI mail clients anymore.
I think you should not put confidential infos in the subject line… :-)
[Clipperz]: How is the random session key generated? Which algorithms and entropy sources are used?
[SR]: It is generated on the server side by GnuPG. So we use the same code and the same algorithms and entropy sources as any other GnuPG-based encryption.
[Clipperz]: Which size is the AES key? Which block cipher mode is implemented?
[SR]: 128-bit and we use CFB.
[Clipperz]: Which size are the asymmetric RSA keys?
[SR]: 1024-bit.
[Clipperz]: Could you provide some information about Freenigma infrastructure? Especially from a security and availability point of view.
[SR]: Security is our main focus, of course. But even if people would be able to steal the servers, they could not access the keyrings, because we don’t store the passwords (mantra). The mantra is only stored in the keyring of every user.
So here we traded convenience against security: When you lose your password, you will never be able to read your old encrypted mails again. Even we can’t help you. But this was important for the overall security. This also means, that nobody else can.
And we don’t log the passwords. We hand them directly over to GnuPG and after the crypto operation they disappear. We (and others) are physically unable to access the keyring.
We know how to build software that runs 24/7, because my company built some very large e-commerce systems in the german speaking market and in Scandinavia. Our customers include the number 2 and 3 Internet-Bookstores, the direct competitors of Amazon.de, so we have experience with robustness and reliability in “uncooperative environments” ;-) .
And now few hints for Gmail users.
- If your account is configured with a custom “From” address, Freenigma won’t work unless you add this address to the list of email addresses in your Freenigma account.
- Freenigma works great even with the hosted domain version of Gmail.
 Mastodon
Mastodon GitHub
GitHub Twitter
Twitter Google
forum
Google
forum